Ever been in the middle of a critical network task, only to realize an IP address you absolutely depended on has vanished into the ether, or perhaps been reassigned without your knowledge? It’s a surprisingly common predicament in the fast-paced world of information security. Whether it’s a server moved to a different subnet, a virtual machine being redeployed, or simply a misconfiguration, a lost IP can throw a serious wrench into your operations, impacting everything from monitoring to access control. This isn’t just an IT nuisance; it has real security implications, creating blind spots or vulnerabilities.
That’s where a clear, concise, and comprehensive process comes into play. Having a standardized way to report, track, and resolve these incidents is paramount for maintaining network integrity and security posture. We are talking about a specific document or procedure that acts as your first line of defense and resolution. A well-designed form can streamline communication, ensure all necessary details are captured, and ultimately help you quickly regain control and visibility over your network assets.

Why a Standardized Approach is Crucial for IP Management in Infosec
In the realm of information security, every piece of data, every asset, and every configuration needs meticulous management. IP addresses are the digital street names of your network; without a reliable system for tracking them, your entire infrastructure becomes difficult to navigate and even harder to secure. A standardized approach, embodied by a dedicated form for lost or changed IPs, transforms a potential chaotic scramble into an organized incident response. It moves beyond just finding the IP to understanding the ‘why’ and preventing recurrence.
Consider the security implications. An untracked or lost IP could belong to an orphaned server still running critical services but no longer monitored. Or, it could be a previously assigned address that’s now free, only to be scooped up by an unauthorized device, creating a shadow IT nightmare. By having a formal process, you ensure that every IP address change or disappearance triggers a predefined set of actions, mitigating these risks proactively. It ensures accountability and reduces the attack surface by identifying and addressing unknown assets.
Beyond direct security benefits, a standardized procedure significantly enhances operational efficiency. Imagine the time saved when technicians arent scrambling to find missing devices or trying to piece together fragmented information from chat messages or hurried emails. With a clear process, information is centralized, making troubleshooting faster and more effective. Furthermore, for compliance frameworks like ISO 27001, HIPAA, or PCI DSS, demonstrating control over your network assets, including IP addresses, is often a requirement. A documented process and usage of a lost ip infosec form template directly contribute to meeting these audit demands.
So, what exactly does a well-crafted form help you achieve when an IP goes missing or is unexpectedly reassigned? It provides a structured framework for data collection and action. Here are some key areas it addresses:
Key Achievements with a Robust IP Change Form
- Rapid Incident Identification: Quickly identify that an IP is no longer where it should be or has been reassigned without proper authorization.
- Detailed Information Capture: Ensure all pertinent details, such as the original IP, new IP (if known), affected system, time of discovery, and reporter’s contact, are recorded.
- Streamlined Communication: Provide a clear channel for reporting these issues to the correct teams (network, security, server admin).
- Root Cause Analysis: Aid in determining why the IP changed or was lost, whether it was human error, system malfunction, or a malicious act.
- Auditable Trail: Create a documented history of the event, which is invaluable for post-incident review and compliance audits.
- Proactive Prevention: By analyzing trends from multiple reports, identify systemic issues that lead to IP management problems and implement preventative measures.
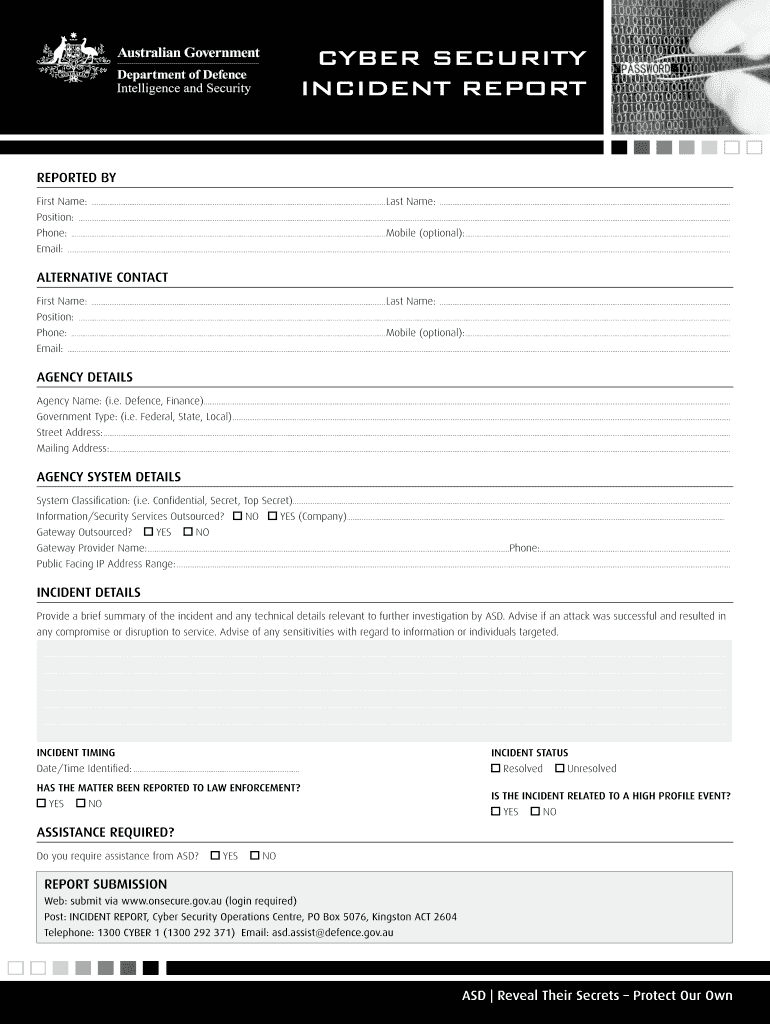
Crafting Your Essential Lost IP Infosec Form Template
Now that we understand the critical importance of a structured approach, let’s talk about what goes into creating an effective lost ip infosec form template for handling lost or changed IP addresses within an information security context. This isn’t just about creating a static document; it’s about designing a tool that facilitates quick action, comprehensive data collection, and seamless inter-departmental collaboration. The ideal template should be intuitive for the reporter and exhaustive enough for the incident response team.
At its core, any good form needs to capture the essentials. Think about what information an analyst would immediately ask for if you walked up to them and said, “I can’t reach server X anymore, its IP is gone!” You’d need to know the ‘who, what, when, where, and why’. This translates into specific fields that guide the reporter to provide all necessary details without ambiguity. It also needs to consider the follow-up actions required, ensuring the form itself prompts the necessary escalation and investigation.
To ensure your form is truly effective and acts as a central hub for incident data, consider including the following crucial fields. The more detail you can capture upfront, the faster the resolution process will be:
- Incident Reporter Details: Name, Department, Contact Information.
- Date and Time of Discovery: When was the IP observed as lost or changed?
- Original IP Address: The IP address that is no longer accessible or has changed.
- Affected System/Device: Hostname, Asset Tag, Type of Device (Server, Workstation, Network Device).
- Expected Location/Service: Where was this IP supposed to be, and what service did it host?
- Observed New IP (if known): If the IP simply changed, what is the new address?
- Description of the Issue: A free-text field for the reporter to explain the situation in their own words.
- Impact Assessment (Initial): What is the perceived impact of this lost IP (e.g., critical service down, minor disruption)?
- Evidence/Logs Attached: A section to indicate if any screenshots, log snippets, or other evidence are attached.
- Actions Taken So Far: What steps, if any, have already been taken by the reporter?
- Priority Level: Based on the impact, what is the urgency?
- Assigned To: (Internal use) Who is responsible for investigating this issue?
- Resolution Details: (Internal use) How was the issue resolved? What was the root cause?
- Date of Resolution: (Internal use) When was the issue resolved?
Beyond just the fields, think about the accessibility and user-friendliness of your form. Is it easily available? Is it integrated into your ticketing system? Providing clear instructions on how to fill it out, what constitutes “lost,” and who to contact for immediate assistance will greatly improve its adoption and effectiveness. Remember, this form is a living document, and its design should evolve as your network and security needs change. Regularly review and update it to ensure it remains a relevant and powerful tool in your infosec arsenal.
In the complex and ever-evolving landscape of information security, meticulous asset management is non-negotiable. While IP addresses might seem like minor details, their accurate tracking and quick recovery when lost are fundamental to maintaining a secure and operational network. Implementing a dedicated process for reporting and resolving these incidents not only enhances your organization’s security posture but also significantly boosts operational efficiency and compliance adherence. It turns a potential crisis into a manageable event.
By investing in a robust framework and utilizing a well-designed template, you empower your teams to act decisively and intelligently when an IP address goes astray. This proactive approach to network visibility and control is a cornerstone of modern cybersecurity, ensuring that your digital infrastructure remains resilient, accountable, and secure against the myriad challenges it faces daily.