Managing access to various areas within any organization, from a small office to a large facility, often boils down to one simple yet critical item: keys. Whether it is for offices, equipment rooms, storage units, or vehicles, keeping track of who has which key and when can become a significant logistical challenge. Without a proper system in place, keys can get lost, misplaced, or even fall into the wrong hands, potentially leading to security risks, operational delays, and unnecessary replacement costs. This is where the need for a streamlined, reliable process becomes incredibly apparent.
Imagine the chaos if keys are simply handed out without any record, or if someone forgets to return a vital key. It can disrupt daily operations and compromise security. A robust key management system is crucial for maintaining order and accountability. Fortunately, you don’t have to start from scratch to build such a system. The solution often lies in adopting a standardized approach, and that’s precisely where a well-designed key check out form template comes into play, offering an elegant way to track, manage, and secure your physical keys efficiently.

Why a Key Check Out Form Template is Essential for Your Organization
In today’s fast-paced environment, many organizations grapple with the challenge of maintaining accurate records of their physical assets, and keys are no exception. Without a formalized system, you might find yourself facing a myriad of issues: uncertainty about who has access to sensitive areas, lost keys leading to costly rekeying, and a general lack of accountability that can breed inefficiency. It is not uncommon for valuable time to be wasted searching for a specific key or trying to ascertain its current whereabouts. This kind of disorganization can lead to significant headaches and even security vulnerabilities.
Implementing a structured approach to key management doesn’t have to be complicated. By utilizing a key check out form template, you immediately introduce a layer of organization and control that was previously missing. This simple yet powerful tool acts as a documented agreement, ensuring that every key transaction is recorded, minimizing the chances of loss, and clearly assigning responsibility. It moves key management from a chaotic free-for-all to a methodical, trackable process, bringing much-needed order to what can often be a overlooked aspect of facility management.
Key Benefits of Implementing a Key Check Out System
The advantages of adopting a standardized key check out form are numerous and impactful for any organization. It transforms a potentially messy situation into a well-oiled machine, contributing positively to various aspects of your operations.
- Enhanced Security: Knowing precisely who has which key at any given moment significantly bolsters your security posture. It discourages unauthorized duplication and provides a clear audit trail in case of a security incident.
- Clear Accountability: Every person checking out a key is formally recorded, making them accountable for its safekeeping and timely return. This reduces instances of misplaced or forgotten keys.
- Improved Efficiency: No more time wasted searching for keys. With a centralized record, you can quickly identify the key’s current holder or its designated storage location. This saves valuable employee time and reduces operational delays.
- Cost Savings: By reducing key loss and the need for frequent rekeying or lock replacements, your organization can realize substantial cost savings over time.
- Compliance and Auditing: A well-maintained log provides excellent documentation for internal audits or external compliance requirements, demonstrating due diligence in asset management.
Ultimately, a dedicated key check out system, built around a reliable template, fosters a culture of responsibility and order. It ensures that critical assets like keys are managed with the care and attention they deserve, safeguarding your premises and operations against potential risks.
What to Include in Your Ideal Key Check Out Form Template
Crafting an effective key check out form template means thinking about all the necessary pieces of information that will make it truly useful for tracking and accountability. It’s not just about jotting down a name and a key number; a comprehensive template ensures that all bases are covered, providing a clear and undeniable record of every key movement. The goal is to create a document that is easy to understand, simple to fill out, and provides all the details you might need later for reference or auditing.
Begin by identifying the absolute essentials. Every form should clearly capture who is taking the key, which specific key they are taking, and when. This core information forms the backbone of your tracking system. Beyond these basics, consider adding fields that clarify the purpose of the key checkout and establish expectations for its return. This foresight can prevent misunderstandings and ensure a smooth process for everyone involved, from the key holder to the administrator.
A well-designed key check out form template will typically include distinct sections to gather all relevant data. Think about how you would describe a key and its movements to someone unfamiliar with your system. What details would they need to understand the transaction fully? This thought process helps in designing a form that leaves no room for ambiguity.
Here are some critical elements you should consider incorporating into your key check out form template:
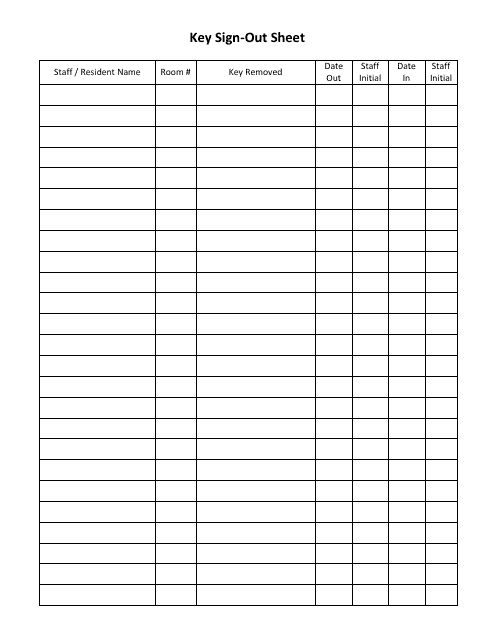
- Key Borrower Information: This includes the full name of the person checking out the key, their department or organizational affiliation, and contact details.
- Key Details: A unique identifier for the key (e.g., key number, code), a brief description of what the key accesses (e.g., "Main Office Door," "Server Room"), and its original location or designated storage.
- Date and Time: Fields for the exact date and time the key is checked out, and crucially, an expected return date and time.
- Purpose of Key Use: A brief explanation for why the key is being checked out (e.g., "After-hours work," "Maintenance," "Temporary access").
- Authorization and Signatures: Spaces for the key borrower’s signature, acknowledging receipt and responsibility, and an authorizing signature from a supervisor or key administrator.
- Return Information: Fields to be filled upon the key’s return, including the return date and time, the name of the person receiving the key, and a signature confirming its return.
- Condition Notes: A small section to note any pre-existing damage to the key or issues upon return.
By including these comprehensive details, your key check out form becomes a robust tool for managing valuable assets, promoting responsible use, and ensuring that your facility remains secure and operations run smoothly without unnecessary interruptions.
Implementing a structured key management system using a dedicated template is a straightforward yet impactful step toward greater organizational efficiency and security. It replaces guesswork with documented facts, fostering a more disciplined approach to how physical access is controlled within your premises. This proactive measure not only safeguards your assets but also contributes to a more organized and accountable work environment for everyone involved.
Ultimately, having a clear, accessible record of key movements eliminates ambiguity, reduces the likelihood of loss, and ensures that critical access points are always monitored. This foresight transforms a potential source of chaos into an area of controlled precision, allowing your organization to operate with greater peace of mind and enhanced operational flow.