In today’s interconnected world, the digital landscape is fraught with potential dangers. From sophisticated cyber attacks to simple human error, the risks to your IT infrastructure are constant and evolving. Without a clear understanding of these vulnerabilities, organizations are essentially navigating a minefield blindfolded. Identifying these threats proactively is not just good practice; it’s a fundamental pillar of modern business resilience.
This is where a structured approach becomes invaluable. Trying to track every potential loophole or incident manually can quickly become overwhelming, leading to oversights and critical gaps in your defense. That’s why having a robust it security risk identification form template is not just a convenience; it’s a strategic necessity. It provides a methodical framework to pinpoint, categorize, and prioritize the dangers that could impact your digital assets, transforming a daunting task into an organized, manageable process.

Why a Structured Approach to IT Security Risks is Non-Negotiable
Imagine trying to fix a leaky roof without knowing where the leaks are or how severe they are. That’s often the chaotic reality for organizations without a proper system for identifying IT security risks. Information security isn’t just about implementing firewalls; it’s about understanding the entire attack surface and the specific threats unique to your operations. Without a structured method, risks are often identified reactively, after a breach has occurred, or are based on anecdotal evidence rather than comprehensive assessment.
An it security risk identification form template brings order to this potential chaos. It acts as a standardized checklist and data collection tool, ensuring that no stone is left unturned. Every potential vulnerability, from network misconfigurations to phishing attempts targeting employees, can be systematically recorded. This consistency is vital because it allows for repeatable assessments and ensures that all relevant stakeholders are considering the same set of parameters when evaluating risks.
The benefits extend far beyond mere documentation. By using a template, you gain a clearer picture of your risk posture, enabling better decision-making regarding resource allocation. You can prioritize which risks to address first, based on their potential impact and likelihood, rather than guessing. This proactive stance significantly strengthens your overall security posture and helps meet compliance requirements from various regulatory bodies that demand demonstrable risk management processes.
Moreover, a well-designed template fosters a culture of security awareness. When teams regularly use an it security risk identification form template, they become more attuned to potential threats, turning every employee into a potential sensor for emerging risks. It transitions the organization from a reactive firefighting mode to a proactive defense strategy, significantly reducing the likelihood and severity of security incidents.
Key Elements to Look for in a Risk Identification Form
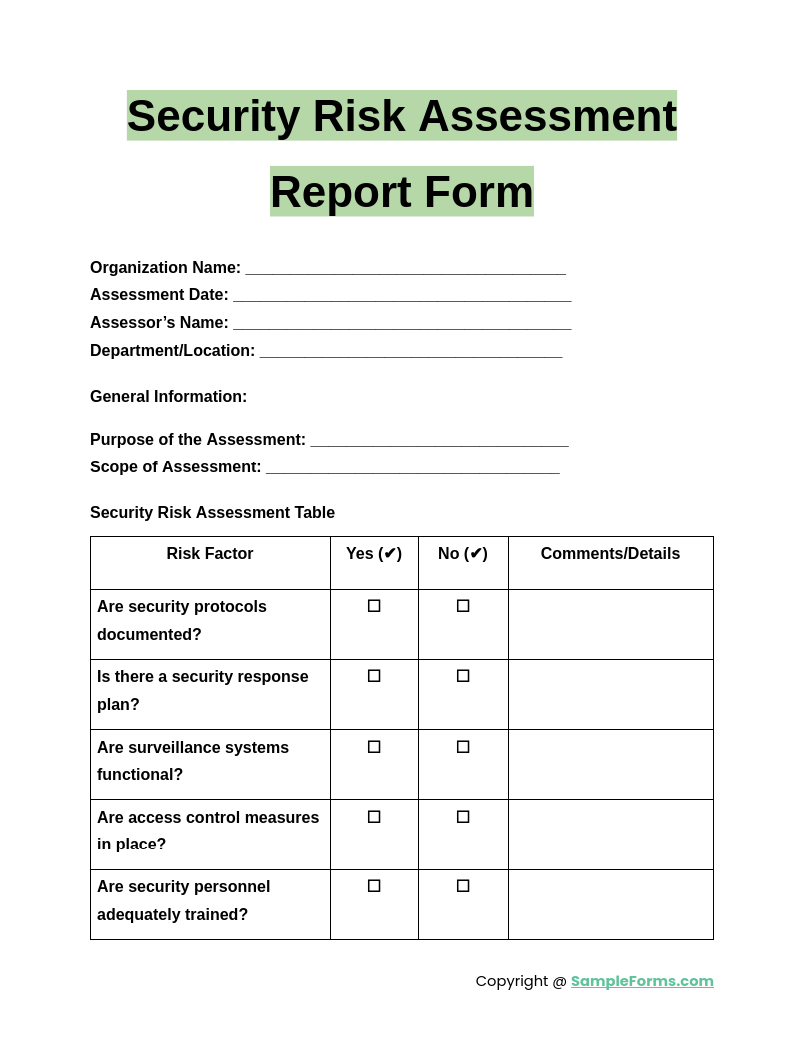
To be truly effective, an IT security risk identification form template should capture specific details that facilitate comprehensive analysis and action. Without these critical components, the form may provide incomplete data, hindering effective risk management. A good template empowers you to not just identify but also understand the nuances of each threat.
- Risk Category: Helps classify the type of risk (e.g., technical, operational, human, compliance).
- Description of the Risk: A clear, concise explanation of the potential threat or vulnerability.
- Potential Impact: Details the consequences if the risk materializes (e.g., data loss, financial impact, reputational damage, operational disruption).
- Likelihood: An assessment of how probable it is that the risk will occur (e.g., high, medium, low).
- Existing Controls: Documents any current measures in place to mitigate the risk, such as firewalls, policies, or training.
- Recommended Actions: Proposes specific steps to further reduce or eliminate the risk.
- Owner: Assigns responsibility for managing and addressing the risk to an individual or team.
- Status: Tracks the progress of risk mitigation (e.g., open, in progress, closed, monitored).
These elements, when thoughtfully completed, transform a simple document into a powerful analytical tool. They provide a structured narrative for each identified risk, making it easier for security teams, management, and even non-technical stakeholders to understand the threat landscape and make informed decisions about mitigating exposures. It’s about turning raw observations into actionable intelligence.
Implementing and Utilizing Your IT Security Risk Identification Form
Having an excellent it security risk identification form template is only half the battle; the real value comes from its consistent and effective implementation. The process isn’t a one-time event but rather a continuous cycle that should be integrated into your organization’s broader security strategy. It requires commitment from all levels, from front-line employees to senior management, to truly embed risk awareness into the company culture.
Start by clearly defining the scope of your risk identification efforts. Will you focus on a specific system, a department, or the entire enterprise? Involve key stakeholders from various departments—IT, legal, HR, operations—as their diverse perspectives can uncover risks that might otherwise be overlooked. Conduct regular workshops or brainstorming sessions where these teams can openly discuss potential vulnerabilities and document them using the chosen form. This collaborative approach ensures a comprehensive view of your risk landscape.
Once risks are identified and documented in the form, the next crucial step is assessment and prioritization. Not all risks are created equal. Use the “potential impact” and “likelihood” fields within your it security risk identification form template to assign a risk score, allowing you to focus resources on the most critical threats first. This helps in developing targeted mitigation plans rather than spreading efforts too thin across less significant concerns. Remember, the goal is to manage risks effectively, not eliminate every single one, which is often an impossible and impractical endeavor.
Finally, the process of using your template should be iterative. The digital threat landscape is constantly changing, with new vulnerabilities emerging and old ones evolving. Schedule regular reviews of your identified risks and update the form accordingly. This might be quarterly, bi-annually, or even more frequently for highly dynamic environments. The form should live and breathe with your organization’s security posture, reflecting ongoing efforts and new challenges. Think of it as a living document that guides your journey toward a more secure digital future.
- Define Scope: Clearly outline what areas, systems, or processes will be assessed.
- Gather Stakeholders: Involve cross-functional teams for diverse perspectives.
- Populate the Form: Systematically record all identified risks using the template.
- Assess and Prioritize: Evaluate risks based on impact and likelihood to determine urgency.
- Develop Mitigation Plans: Create actionable strategies to address high-priority risks.
- Monitor and Review: Continuously track risk status and reassess as the environment changes.
Effective utilization of an IT security risk identification form doesn’t just catalog problems; it empowers an organization to proactively manage its digital destiny. By embedding this systematic approach into daily operations, businesses can build a more resilient foundation, ready to face the complexities of the modern cyber world with confidence and control. This ensures that security becomes an enabler of business, rather than a hinderance, by creating a clear pathway to protection.
Embracing a systematic approach to identifying IT security risks is a cornerstone of robust organizational defense. It transforms what could be a reactive, overwhelming challenge into a structured, manageable process, enabling businesses to proactively address vulnerabilities before they escalate into costly breaches. By fostering a culture of continuous assessment and diligent documentation, organizations can significantly enhance their resilience in an increasingly complex digital landscape.
Ultimately, investing time in a well-implemented risk identification framework is an investment in future stability and operational continuity. It positions your enterprise not just to survive the evolving threat landscape but to thrive within it, confident in the strength of your foundational security practices and your ability to adapt to new challenges.