In today’s interconnected world, secure remote access is no longer a luxury but a fundamental necessity for businesses of all sizes. As more teams work remotely, and as organizations collaborate with external partners, ensuring data integrity and confidentiality across various networks becomes paramount. IPSec VPNs offer a robust and secure method for establishing these connections, encrypting data in transit and authenticating both ends of the communication. However, managing requests for new VPN access can quickly become a bottleneck, leading to confusion, delays, and potential security vulnerabilities if not handled systematically.
Without a clear, consistent process, IT departments often find themselves sifting through fragmented emails, incomplete tickets, and verbal requests. This ad-hoc approach wastes valuable time, increases the risk of misconfigurations, and makes it challenging to maintain an accurate record of who has access to what, and why. This is precisely where a well-designed ipsec vpn request form template steps in, transforming a potentially chaotic process into a streamlined, secure, and efficient operation that benefits everyone involved.

Why a Standardized IPSec VPN Request Form is Essential
Implementing a standardized request form for IPSec VPN access brings immediate and significant improvements to an organization’s IT operations and overall security posture. First and foremost, it ensures that all necessary information is collected upfront. This eliminates the back-and-forth communication often required to gather missing details, dramatically speeding up the provisioning process. When IT teams receive a comprehensive request, they can move directly to evaluation and implementation, rather than spending time chasing down basic information.
Furthermore, a consistent template helps enforce security policies and compliance requirements. By including fields for justification, approval workflows, and specific technical parameters, organizations can ensure that every VPN request aligns with their security standards and audit trails are easily maintained. This proactive approach minimizes the chances of unauthorized access or misconfigured connections that could expose sensitive data to risk. It’s about building security into the very first step of granting network access.
Key Elements to Include in Your Template
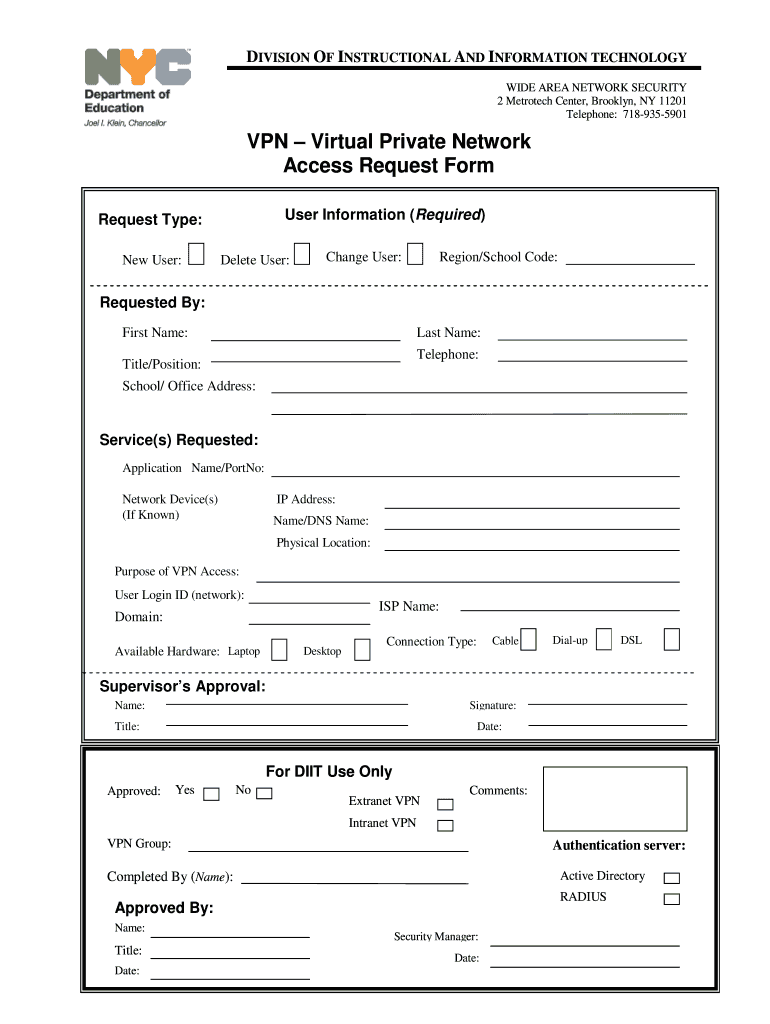
- Requester Information: Full name, department, contact details.
- VPN Purpose and Justification: Clear explanation of why VPN access is needed (e.g., remote work, partner access, specific project).
- Required Access Type: Specify if it’s user-based, site-to-site, or a particular application access.
- Technical Specifications: Local network IP range, remote gateway IP, authentication method (pre-shared key, certificates), encryption algorithms (AES256, SHA256), tunnel mode (transport, tunnel), NAT traversal, DPD (Dead Peer Detection) settings, tunnel lifetime.
- Duration of Access: Indicate if access is temporary or permanent.
- Approval Sign-off: Section for managerial or security team approval.
Having detailed technical fields is particularly crucial for IPSec VPNs due to their inherent complexity. Accurate IP addresses, subnet masks, encryption protocols, and authentication methods are vital for establishing a successful and secure tunnel. A well-structured template guides the requester to provide these specifics, reducing the likelihood of configuration errors during deployment. It serves as a blueprint for the IT administrator, ensuring that all technical requirements are explicitly laid out before any work begins.
Finally, a standardized form contributes to a robust audit trail. Every completed form serves as a record of who requested access, why, when it was approved, and what technical parameters were implemented. This documentation is invaluable for internal audits, compliance checks, and troubleshooting. Should an issue arise or a security incident occur, the forms provide a clear history, aiding in investigation and accountability. It transforms a scattered set of interactions into a structured, auditable process.
Building Your Effective IPSec VPN Request Process
While having a great ipsec vpn request form template is a fantastic start, its true power comes from integrating it into an efficient request and approval workflow. Simply providing a form isn’t enough; organizations need to define the steps from submission to provisioning clearly. This includes specifying who needs to approve requests, what technical reviews are required, and how the approved access will be implemented and communicated to the user. A well-defined process ensures consistency and reduces potential delays caused by ambiguities in the workflow.
Consider digitizing your form using internal IT service management (ITSM) tools or simple online form builders. This approach can automate parts of the workflow, such as routing requests to the appropriate approvers or creating an IT ticket automatically upon submission. Digital forms also make it easier to track the status of a request in real-time, provide notifications, and maintain a centralized database of all VPN access requests. This significantly improves transparency for both the requester and the IT team.
Training and communication are also vital for the success of any new process. Ensure that employees understand where to find the form, how to fill it out correctly, and what to expect after submission. Providing clear guidelines and perhaps even a brief tutorial can minimize errors and frustration. When users are empowered to submit complete and accurate requests, the entire system benefits, leading to faster service delivery and happier end-users. It fosters a collaborative environment where security is a shared responsibility, understood by everyone.
By embracing an ipsec vpn request form template as part of a well-defined process, organizations can not only enhance their security posture but also significantly improve operational efficiency. It moves the IT department from a reactive state, constantly firefighting incomplete requests, to a proactive one, where secure access is managed systematically and predictably. This structured approach allows IT to focus on strategic initiatives rather than administrative overhead, contributing directly to the company’s productivity and resilience in a connected world.